Microsoft Defender for Identity (MDI) is the successor of the on-premises Advanced Threat Analytics (ATA) product. It is cloud based security solution for on-premises Active Directory and ADFS services.
Microsoft Defender for Identity helps detect attacks like Pass The Hash, the recent PrintNightmare and PetitPotam vulnerabilities, Golden Ticket attacks, various reconnaissance activities like the enumeration of domain admins, and much more.
Architecture of Defender for Identity
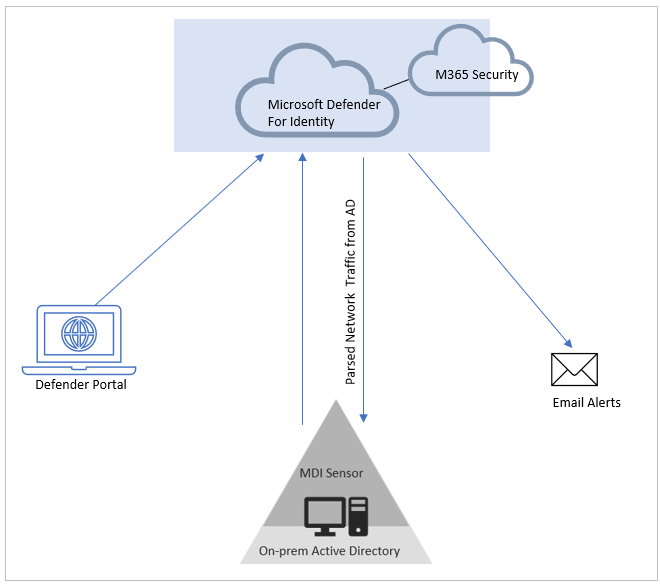
Defender for Identity requires to install sensor on AD to phrase traffic. Following are two types of sensors available
- Regular sensor, which is the default experience when you install the agent (sensor) directly onto a Domain Controller or AD FS server.
- Standalone sensor, whereby the agent (sensor) is installed on a dedicated/separate server in the environment which received a copy of the network traffic of the Domain Controller(s) or AD FS servers via Port Mirroring.
Pre-requisites for Defender for Identity
- Initial Configuration in the Tenant for MDI
- Enable connectivity from Domain controllers to MDI endpoints
- Service Accounts (Preferred Group Managed Service Accounts)
- Enable auditing and logging in the Active Directory
- Install MDI sensor in the Domain controller
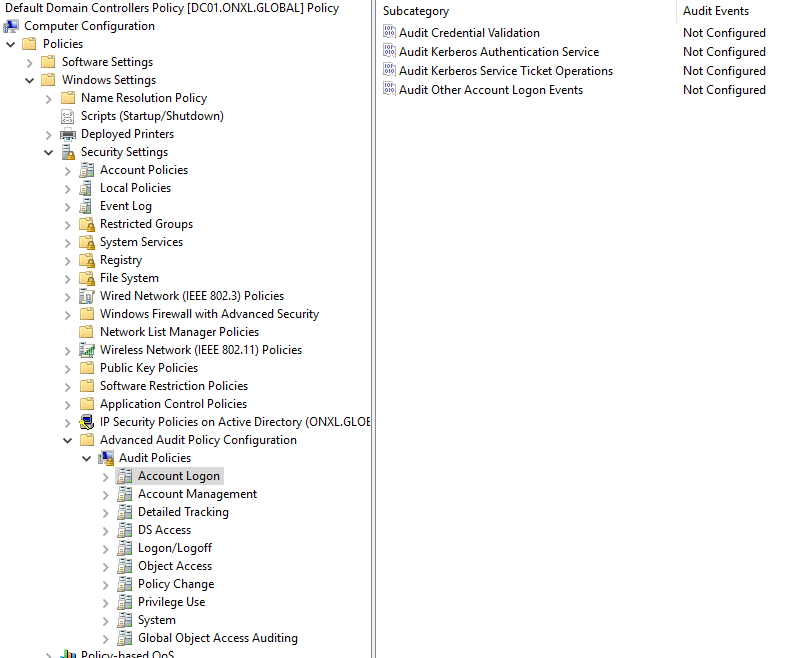
Enable required auditing and logging in the Active Directory from the Group policy management console
Computer Configuration -> Windows Settings -> Security Settings -> Audit Policies -> Audit Credential Validation
(Success & Failure Events)
Audit Event ID 8004
Security policy setting Value
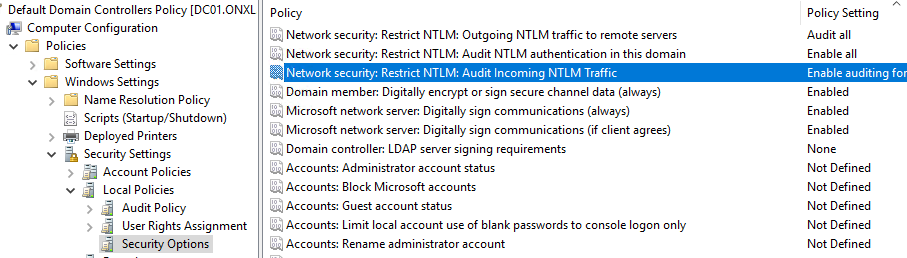
| Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers | Audit all |
| Network security: Restrict NTLM: Audit NTLM authentication in this domain | Enable all |
| Network security: Restrict NTLM: Audit Incoming NTLM Traffic | Enable auditing for all accounts |
Configure Object auditing Event 4662 events are also necessary to configure object auditing on the user, group and computer objects.

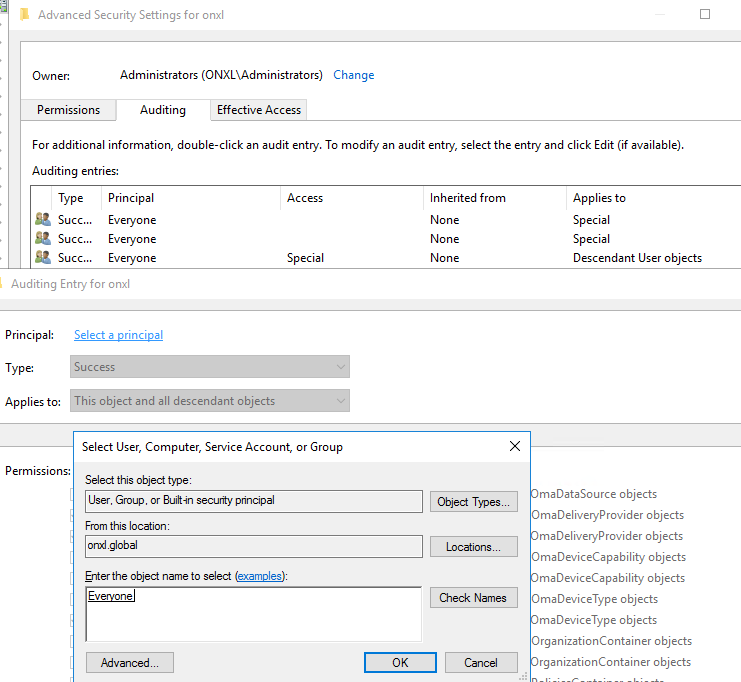
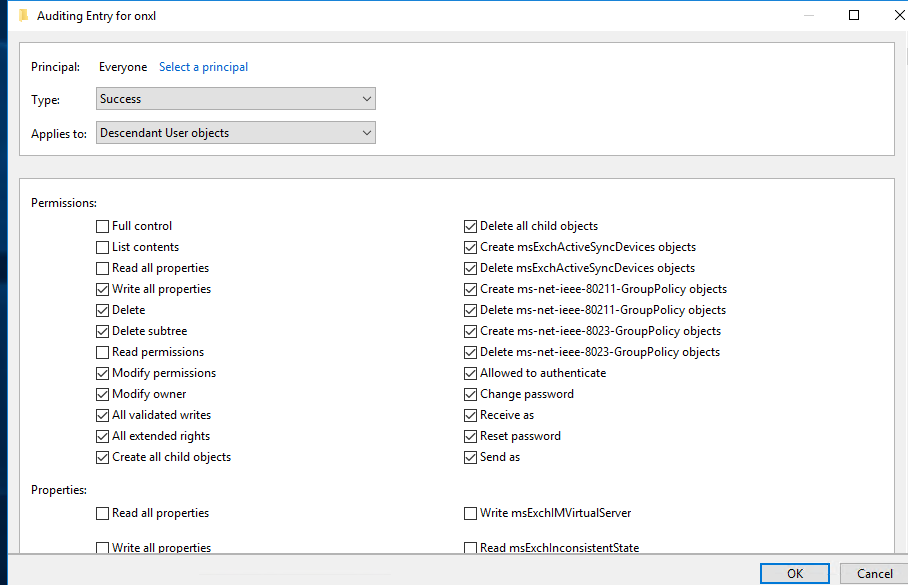

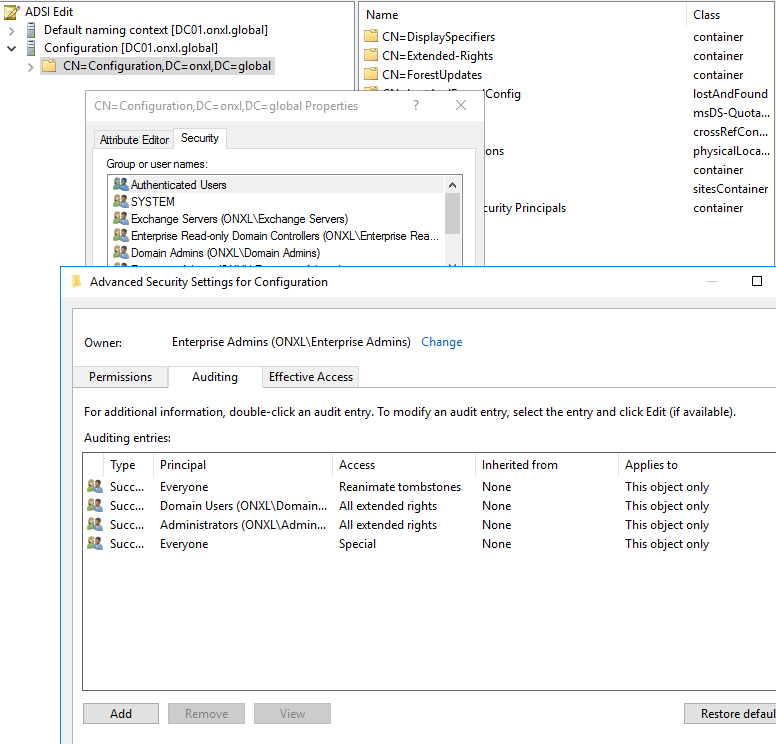
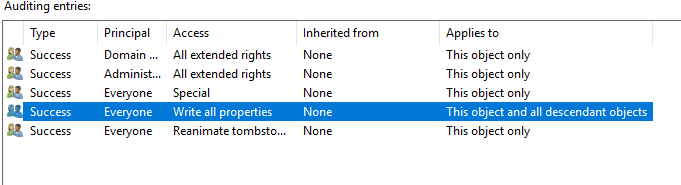
Enable Auditing on the Active Directory Configuration container
Open ADSIEDIT.msc
Create Service account For MDI sensor
Group Managed Service Account create from Powershell
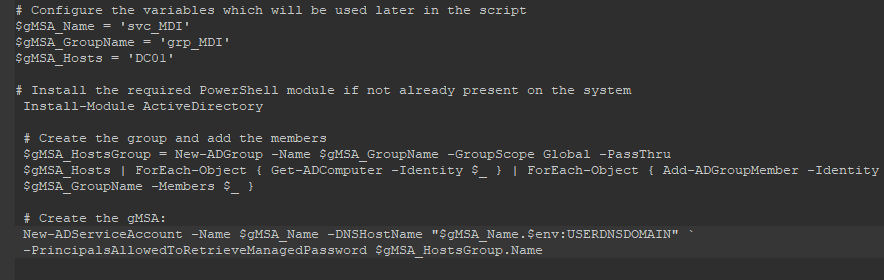
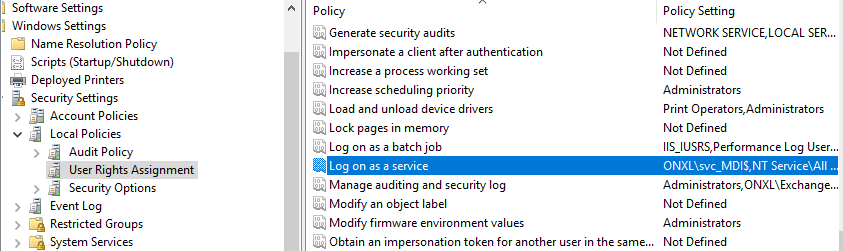
Add the gMSA account in the Log on as a service
Install MDI sensor in the DC server.

Login to Microsoft 365 Defender portal then settings click on Identities

Click on Add sensor then download the installer agent.
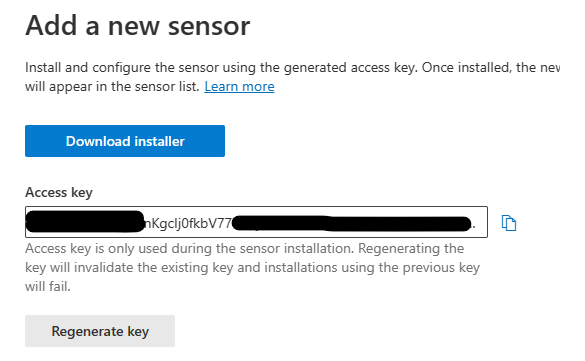
Copy the Access Key and it required for sensor agent configuration.

Run the sensor agent tool in Domain Controller, During the installation process Access Key needs to be entered.


Finish the MDI sensor setup

Login the Defender portal and verify the sensor service status.

In this exercise MDI agent is installed directly on the Domain controller (Regular sensor). Event alerts will be available in the Defender portal alerts section