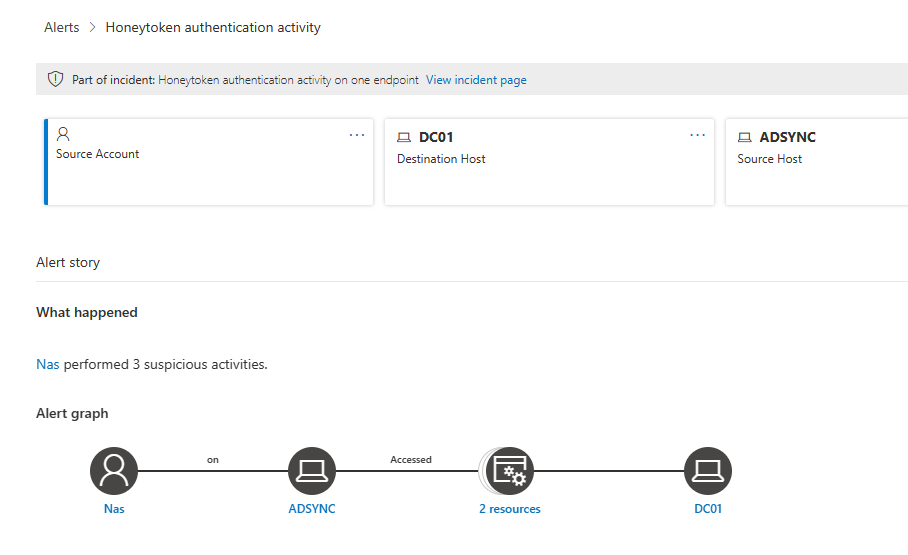
Honeytoken accounts are accounts that are used to mislead bad actors. They exist to make an attacker believe the account is real and can be exploited, whereas it’s nothing more than a stale account, waiting for someone to try and use it. As a honeytoken account is somehow used, abused, or otherwise manipulated, an alert is immediately triggered.
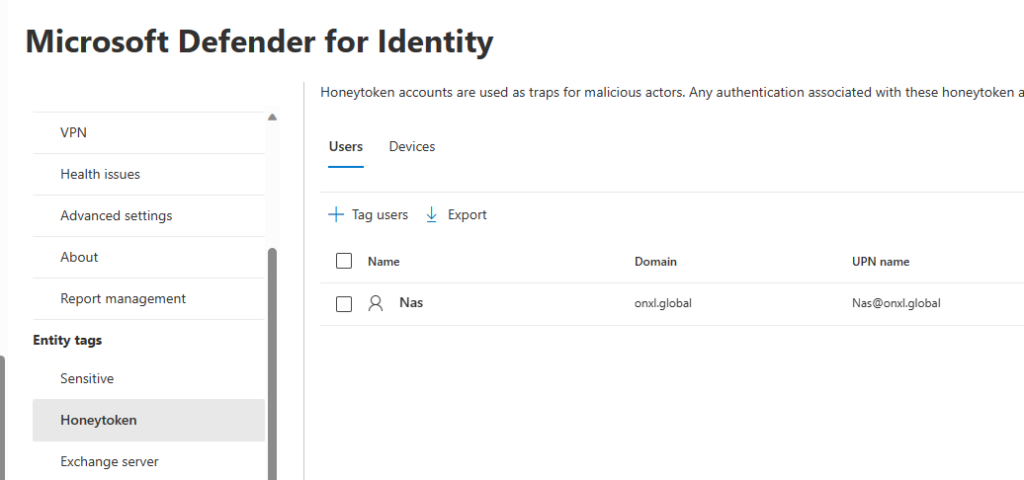
Manually tagging identities or clients as honeytoken can be done from the Microsoft 365 Security Center. When choosing the accounts to be used make sure to use an attractive name. Within the Microsoft 365 Security Center, click Settings > Identities. Under Entity tags, click Honeytoken, and finally click Tag users to select which users to tag as a Honeytoken account. The same procedure can be used to tag devices too.
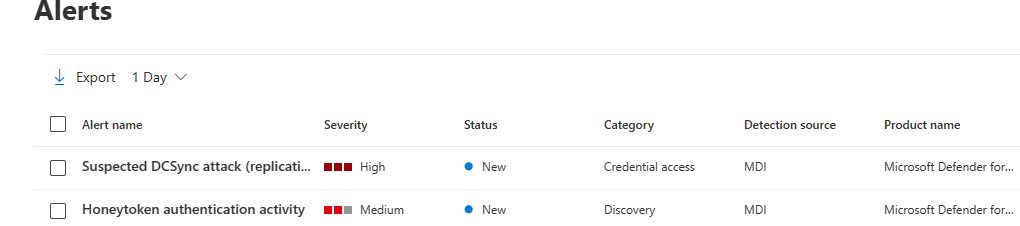
When the honeytoken user or device is used to authenticate, an event will become visible on the Timeline of the Microsoft Defender for Identity portal. Click the event to analyze what happened with the Honeytoken account